How Israeli regime is trying to censor internet after massive hack of sensitive data
By Ivan Kesic
Over the past several months, since the launch of the genocidal war against Palestinians in Gaza, foreign hackers have successfully infiltrated Israeli computer systems, accessing troves of classified and sensitive data.
This material, comprising gigabytes of diverse information, represents the largest information leak in the history of the Israeli regime, according to military and intelligence officials cited in a report by the Israeli newspaper Haaretz.
The attacks targeted a wide range of departments in the occupied territories, from military and defense contractors to municipalities, hospitals, and ministries, as well as important organizations that interact with them.
Non-regime and individual targets were also affected, including the accounts of Israeli regime politicians, military officials, and the servers of private companies in the occupied land.
The types of cyberattacks recorded range from classic denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks to sophisticated malware that penetrates systems, disrupts networks and gathers sensitive information.
Israeli military sources report that these attacks are becoming more sophisticated, with hackers using Israeli IP addresses to bypass defenses designed to protect against foreign threats.
While major organizations affiliated with the regime in Tel Aviv, such as ministries, have robust cyber defenses, lower-tier institutions and municipalities remain vulnerable, making them prime targets of such hacking attacks.
Equipping all 300 entities classified by the Israeli regime as "critical organizations" with adequate cyber security measures requires significant time and resources, the hiring of new experts, and multi-billion dollar investments.
The extent of the breach has overwhelmed existing cyber security infrastructure in the occupied territories, and the true scale of the damage remains difficult to ascertain as the regime tends to systematically downplay and cover up the damages.
In mid-July, Col. Racheli Dembinsky, commander of the Israeli military-affiliated Center of Computing and Information Systems (Mamram), reported that their cloud computing network had faced over three billion cyberattacks since the war on Gaza was launched.
These attacks targeted operational cloud computing systems used by troops on the ground to share information and coordinate the locations of forces.
That same week, the regime's Cyber Emergency Response Team (CERT) reported 1,900 significant cyber attacks against companies across the occupied territories since October 2023, noting that the nature of the attacks has evolved with time.
CERT highlighted an increase in ransomware attacks designed to damage the regime infrastructure, which has already suffered amid the protracted war now in the 12th month.
Targets of cyber attacks
Earlier in May, the Israeli regime reported 120 cyber attacks on municipalities, with local media identifying at least five successful breaches, including the notable hacking of the Zionist settlement of Modi'in Ilit.
The city of 84,000 settlers was the target of a sophisticated cyber attack in January, which crippled the municipal computer system for a month, completely blocking access to documents, emails, payments, taxes, bills, and services.
Journalists who investigated the case reported an atmosphere of fear, with all employees seemingly under Israeli military directives to remain tightlipped about the details.
In March, the hacktivist group DarkBit, which operates under the slogan "against racism, fascism, and apartheid," reported the successful hacking of the Tel Aviv Municipality, despite its much-hyped cyber defenses.
The group also targeted two other regime agencies: the so-called Israel National Cyber Directorate and the Ministry of Health's mental health division.
"We hacked the Israel National Cyber Directorate (INCD) or, more precisely, the 'Israel National Center of Dummies' – the center for a bunch of idiots," DarkBit wrote at the time.
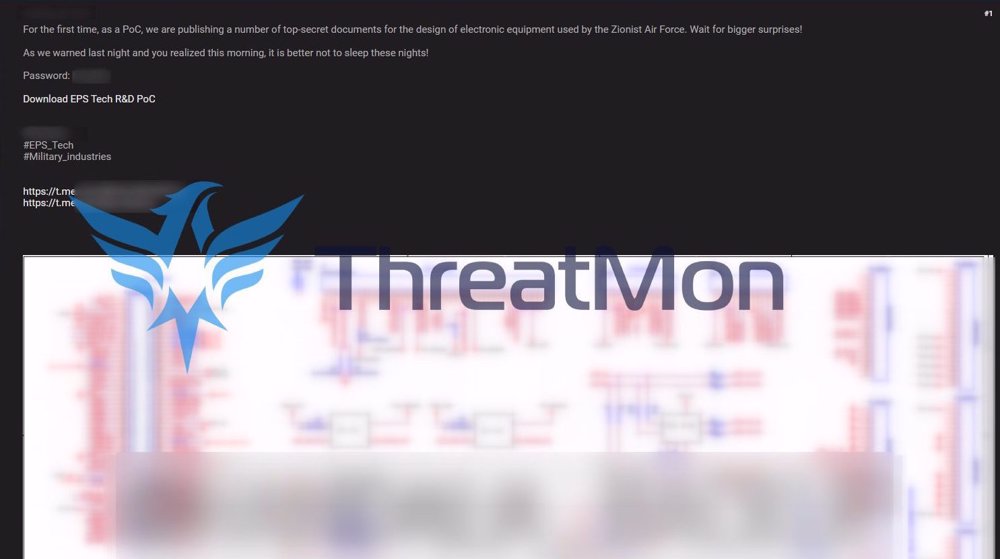
Other hacker groups disclosed sensitive information obtained from hacking the so-called Dimona Negev Nuclear Research Center, the National Insurance Institute, the Ministry of Justice, and the Ministry of Military Affairs, the latter confirmed by officials.
The hacked files from the military affairs ministry included cooperation agreements, technical drawings for military devices, weapons, parts, and even documents related to the regime’s Iron Dome air defense system, which has been depleted and overwhelmed amid war.
The regime authorities attempted to downplay the significance of the leak, claiming that the documents were "old and from an outdated system," but the leaked data revealed personal details of senior officials and included sensitive documents and email exchanges.
In November, hackers also targeted the Israel regime archives department, which houses some 400 million documents, and the archive was only restored online in June.
Health centers, including hospitals in the occupied cities of Haifa and Safed, were also targeted. From the latter, previously known for treating Takfiri terrorists from Syria, 500 gigabytes of patient data, including 100,000 medical records linked to military personnel, were hacked.
These attacks have caused enormous damage, which the so-called National Cyber Directorate estimated in May at 12 billion Shekels ($3.3 billion) annually, though unrecognized cyber damage likely means the true losses are much higher.
Israel's international reputation has also taken a significant hit, as the regime's propaganda has long branded itself as a technological giant and the most advanced cyber power in the region—a claim now increasingly questioned and effectively debunked.
Israel's response to leaked data
The goals of these hacker attacks vary, including intelligence gathering, disrupting infrastructure and services, and exposing sensitive data to embarrass and demoralize the regime and entities and individuals affiliated with it.
Financial and reputational damage to Israeli regime companies, particularly those with strong ties to the political apparatus in Tel Aviv and the military, is also a key objective.
The data leaks serve as a form of psychological warfare, instilling public panic and creating a sense of vulnerability.
After hackers obtained massive amounts of classified Israeli regime data, many sought to spread the information to the widest possible audience, often using social media platforms.
The Israeli regime, aware that it cannot entirely prevent public data leaks, focused on minimizing the publication of such data and mitigating the long-term damage caused by its online presence.
As Haaretz noted, Israel's approach is unique in that it does not target hackers with lawsuits, as they are mostly beyond its reach. Instead, it focuses on publicly available content.
While the United States and other countries typically initiate legal proceedings against leakers, both domestic and foreign, and accept the inevitable online existence of leaks, Israel uses tech companies' internal rules to remove online content.
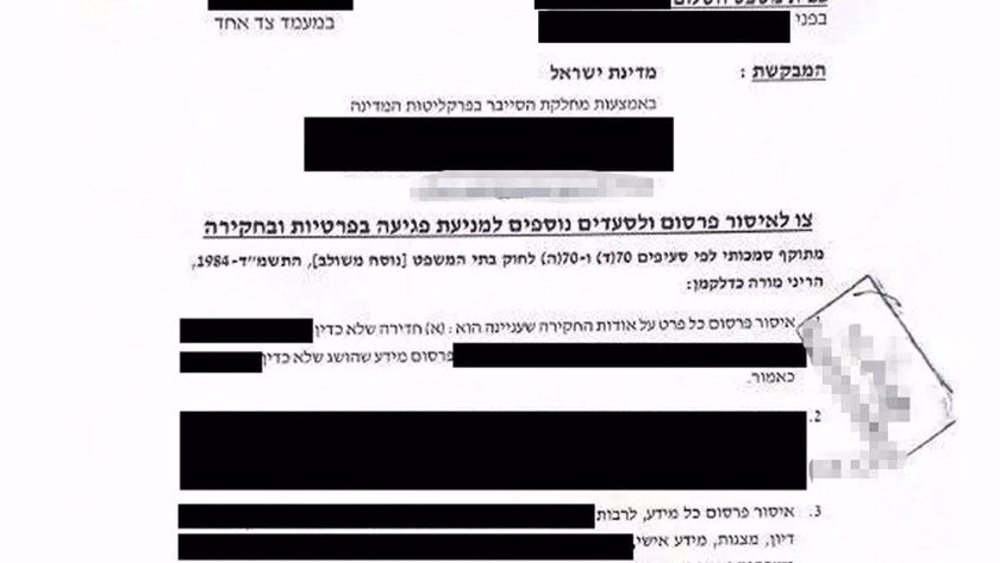
Hundreds of digital soldiers actively monitor the web and social networks, reporting any appearance of leaked material as a violation of terms of use to help centers.
This approach is often successful with tech giants, who have strict rules about copyright, libel, and stolen goods, categories that broadly include hacked material.
Moreover, US giants such as Google, Amazon, Meta, and X (formerly Twitter) are known for their overt pro-Israel bias and are subject to Israeli political pressure.
According to official numbers provided by the Israeli regime, Facebook alone removed over 40,000 pieces of so-called "illegal content" at the request of the regime’s ministries, and even TikTok took down over 20,000 posts.
These Israeli-backed activities have sparked a cat-and-mouse game with hackers, who have developed more effective methods for disseminating leaked data on popular social networks and more advanced technological means to create websites that cannot be taken down.
This has also led to an ongoing legal battle in France, where the director of a mega-popular social network with nearly a billion users refused to comply with Israeli demands.
Telegram's resistance to Israeli pressure
Telegram, originally a Russian messaging service based in the UAE, has proven to be the most resistant to pressure from the Israeli and Western regimes to censor content they find objectionable.
As a result, Telegram has become a key platform for anti-Israel content, which the Israeli regime has struggled to control or monitor, as witnessed since October 7 last year.
While many tech giants have streamlined mechanisms through which they can be reached, Telegram is considered the least option, even when direct requests are made to its CEO and co-founder, Pavel Durov.
Compared to other social networks that removed tens of thousands of critical posts at the request of the Israeli regime, Telegram responded positively to similar requests only 1,300 times, likely based on its rules regarding stolen goods.
Even after several takedowns of hacker groups' accounts and channels, Telegram users quickly and easily created new channels and reposted links to the same leaked data, frustrating Israeli regime authorities.
Tech giants like Google, Meta, and Amazon regularly remove online material related to Palestinian resistance movements, which their host countries blacklist, but this is not the case with Telegram.
Furthermore, unlike other platforms with extensive networks of content moderators, Telegram offers only a single email address for complaints from entities and individuals alike.

With no other solution and frustrated by the increase in pro-Palestinian material, in late 2023, the Israeli regime, through intermediaries in the tech industry, attempted to contact Durov privately, who resides in Dubai.
This recalls a similar effort around the same time when the Israeli regime sought to contact Elon Musk and bring him to the occupied territories for a meeting with Prime Minister Benjamin Netanyahu, due to concerns over the growth of anti-Israel posts on his X platform.
Although they eventually made contact with Durov, he ignored their requests to tighten Telegram's moderation, and according to Haaretz, the Israeli initiative failed.
In April, Durov stated that he was being pressured by unnamed entities but insisted that Telegram should remain a neutral platform, not a player in global geopolitics.
Durov was finally arrested ten days ago upon landing in Paris, where he was taken into custody on unsubstantiated charges that Telegram was aiding illegal activities.
The prosecutor’s statement announced that Durov faces 12 separate charges, including "refusal to communicate, at the request of competent authorities, information or documents necessary for carrying out and operating interceptions allowed by law."
“If Pavel Durov could be arrested on these charges, then any country can arrest the leaders of Facebook, Google, Apple, Microsoft…any tech company that helps people communicate,” columnist and blogger S. L. Kanthan wrote in a post on X.
“France is a puppet of USA and Israel, who are mad at not having a backdoor to Telegram.”
Press TV’s website can also be accessed at the following alternate addresses:






 This makes it easy to access the Press TV website
This makes it easy to access the Press TV website